前言
记录2023年金砖初赛RE解题WP。
re1203
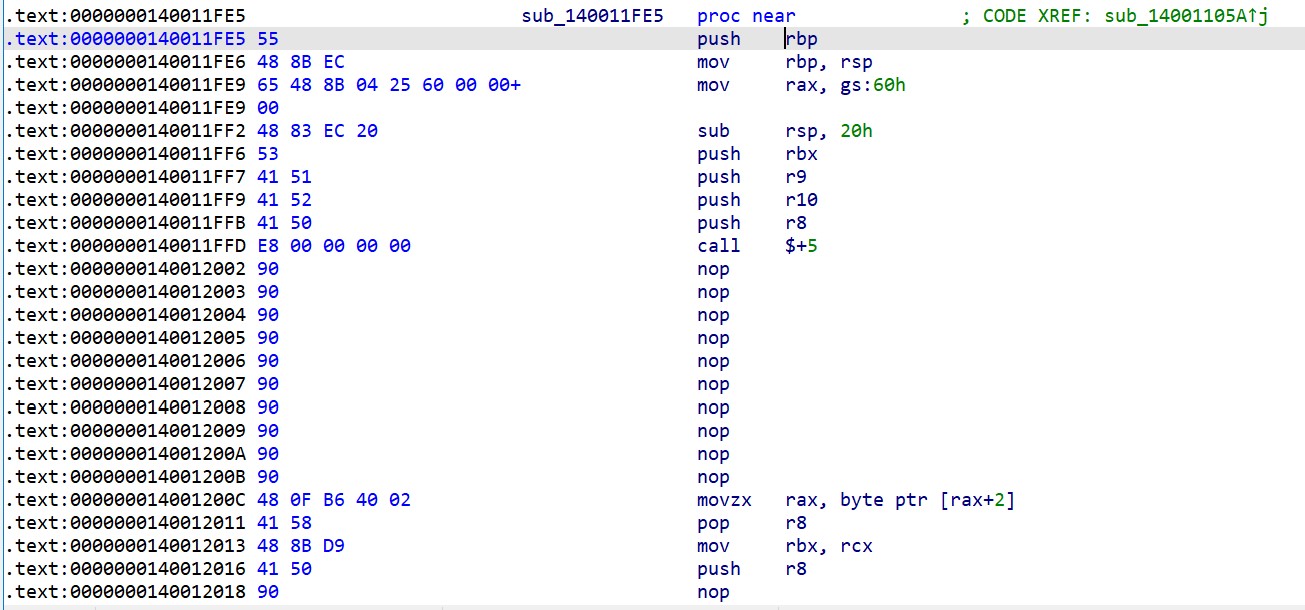
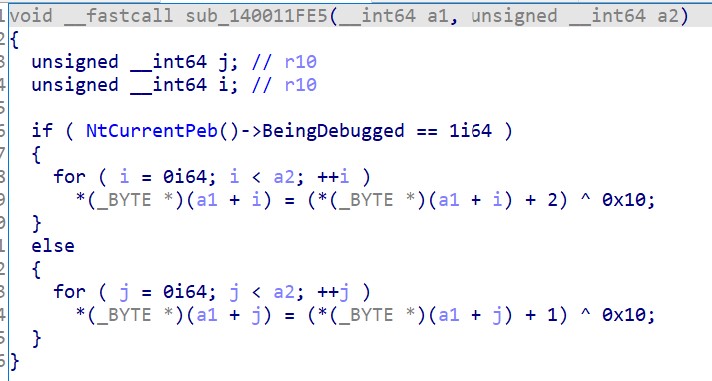
加了点简单的花指令,去花后得到密钥生成流程和加密方法。 花指令如下:
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
int main()
{
unsigned char v10[15] = "High_Ground";
unsigned char final[40] = {
0x3F, 0x16, 0x19, 0x1E, 0x0B, 0x6B, 0x01, 0x51, 0x5E, 0x46, 0x42, 0x61, 0x19, 0x1E, 0x41, 0x14,
0x6D, 0x55, 0x54, 0x51, 0x4C, 0x13, 0x6D, 0x4D, 0x41, 0x40, 0x43, 0x6D, 0x01, 0x56, 0x57, 0x4D,
0x47, 0x6C, 0x4F, 0x1A, 0x49, 0x0D};
unsigned char flag[40] = {'\0'};
int v11 = strlen(v10);
for (int j = 0; j < v11; ++j)
v10[j] = (v10[j] + 1) ^ 0x10;
int a2 = 38;
int v12 = 0;
while (v12 < a2)
{
flag[v12] = final[v12] ^ v10[(int)v12 % (int)v11];
++v12;
}
printf("%s\n", flag);
return 0;
}JLRE0203
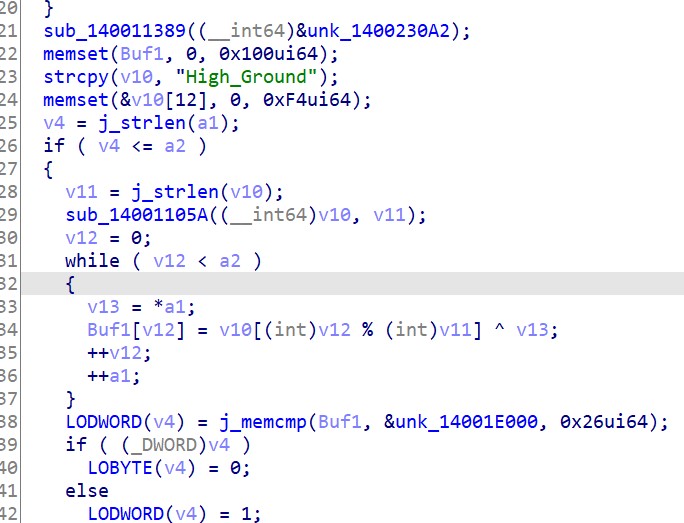
当时没做出来,只知道是SMC,赛后看了官方wp,得知程序中的长串字符为经过异或加密后的代码,key为2byte,通过分析出现频率最高的2byte字符,可以猜测其为key(因为机器指令中地址占大头,而且地址中存在较多的00,由此key xor 00=key)。得知key为hi(小端模式),dump出SMC并异或解密,得到加密代码。 解密SMC代码如下:
#include <stdio.h>
int main()
{
unsigned char data[100] = {
0x29, 0x3E, 0x29, 0x3F, 0x21, 0xE0, 0xA7, 0x28, 0xE8, 0xAE, 0x7D, 0x20, 0xE9, 0x8E, 0x97, 0x69,
0x68, 0x69, 0x21, 0xEA, 0x8F, 0x66, 0x21, 0xE0, 0xA6, 0x20, 0xE9, 0x8F, 0x97, 0x69, 0x68, 0x69,
0x21, 0xA8, 0x96, 0x6D, 0x21, 0xEA, 0x8E, 0x66, 0x21, 0xA8, 0x8F, 0x6D, 0x25, 0x60, 0x96, 0x25,
0xE1, 0x99, 0x6C, 0x7F, 0x5C, 0x7F, 0x29, 0x37, 0x29, 0x36, 0xEB, 0x26};
for (int i = 0; i < 60; i++)
{
if (i % 2 == 0)
{
data[i] = data[i] ^ 0x68;
}
else
{
data[i] = data[i] ^ 0x69;
}
}
FILE *file;
file = fopen("output.bin", "wb");
fwrite(data, 1, 60, file);
return 0;
}output.bin文件经过ida反汇编可以得到大概的加密逻辑如下: